会员
周边
众包
新闻
博问
闪存
所有博客
当前博客
a56爆大奖在线娱乐的博客
a56爆大奖在线娱乐的园子
账号设置
简洁模式
...
退出登录
注册
登录
DirWangK
勿在浮沙筑高台
博客园
首页
新随笔
联系
订阅
管理
perlapp exe 分析
# 通过script定位 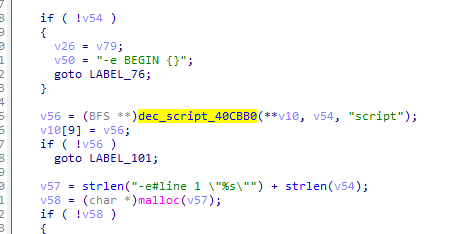 # 跟进,定位extract ```c++ void *__fastcall
posted @
2023-08-20 21:14
DirWangK
阅读(
24
) 评论(
0
)
编辑
收藏
举报
会员力量,点亮园子希望
刷新页面
返回顶部
公告